1. OpenLDAP
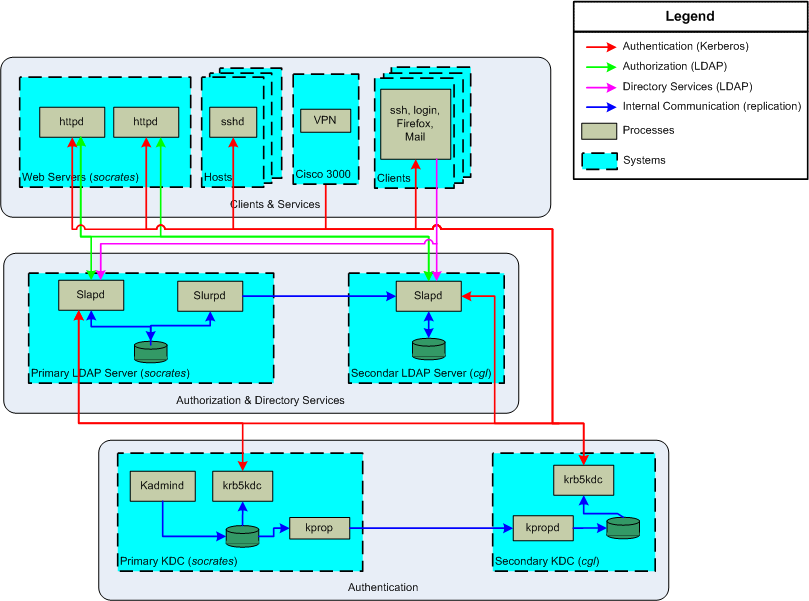
As Kerberos forms the basis of our approach to authentication,
LDAP forms the basis of our approach to authorization. The LDAP
technology we use is the OpenLDAP server, which can be found
at http://www.openldap.org.
This open source package is extremely robust and forms the core
of many commercial products and is explicitly supported by
several vendors. This broad level of support and ongoing development
by a significant community results in a variety of documented
uses on the Internet, including serveral "HOWTO's". For our
implementation, we have deployed the OpenLDAP servers on two hosts,
similar to our deployment approach to Kerberos. Like Kerberos, our
master server runs on socrates.cgl.ucsf.edu in a clustered
environment under CAA control. The division of functionality is
somewhat different in an LDAP environment than in a Kerberos
environment. OpenLDAP provides two different servers, slapd,
which answers all LDAP queries, including updates and new entries,
and slurpd, which replicates data between the master server
and the slave. All functions are controlled by the main configuration
file, slapd.conf, which is shown below.
#
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
loglevel 256
#
# Load all schemas
#
include /usr/local/etc/openldap/schema/core.schema
include /usr/local/etc/openldap/schema/misc.schema
include /usr/local/etc/openldap/schema/cosine.schema
include /usr/local/etc/openldap/schema/inetorgperson.schema
include /usr/local/etc/openldap/schema/nis.schema
include /usr/local/etc/openldap/schema/kerberosobject.schema
include /usr/local/etc/openldap/schema/eduPerson.schema
include /usr/local/etc/openldap/schema/ucsfPerson.schema
include /usr/local/etc/openldap/schema/cglaccount.schema
include /usr/local/etc/openldap/schema/mozilla.schema
# Define global ACLs to disable default read access.
# Global directives
allow bind_v2
sizelimit 10000
pidfile /var/run/slapd.pid
argsfile /var/run/slapd.args
# Load dynamic backend modules:
modulepath /usr/local/libexec/openldap
moduleload pw-kerberos.so
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 63-bit encryption for simple bind
# security ssf=1 update_ssf=56 simple_bind=56
defaultsearchbase dc=cgl,dc=ucsf,dc=edu
# SASL directives
# srvtab /etc/krb5.keytab
sasl-realm CGL.UCSF.EDU
sasl-host socrates.cgl.ucsf.edu
# TLS directives
TLSCertificateFile /usr/local/etc/openldap/slapd.crt/server.crt
TLSCertificateKeyFile /usr/local/etc/openldap/slapd.key/server.key
#
# Provide ability for owners to edit their own group
#
access to dn.subtree="ou=Web Groups,ou=Groups,dc=cgl,dc=ucsf,dc=edu" attr=memberUid,owner,description,entry
by dnattr=owner write
by group="cn=LDAPAdmin,dc=cgl,dc=ucsf,dc=edu" write
by * read
# Access control for private fields in People
# Should be readable by staff, writable by LDAPAdmin or the user
access to dn.subtree="ou=UCSF,ou=People,dc=cgl,dc=ucsf,dc=edu"
filter=(cglPrivate=TRUE)
attr=homePhone,homeTelephoneNumber,mobile,mozillaHomeCountryName,mozillaHomeLocalityName,mozillaHomePostalCode,mozillaHomeState,mozillaHomeStreet,mozillaHomeStreet2,mozillaHomeUrl,mozillaNickname
by dnattr=seeAlso write
by group="cn=LDAPAdmin,dc=cgl,dc=ucsf,dc=edu" write
by group="cn=staff,ou=UNIX Groups,ou=Groups,dc=cgl,dc=ucsf,dc=edu" read
by users none
by anonymous none
# Access control for private fields in People that are set as non-Private
access to dn.subtree="ou=UCSF,ou=People,dc=cgl,dc=ucsf,dc=edu"
filter=(cglPrivate=FALSE)
attr=homePhone,homeTelephoneNumber,mobile,mozillaHomeCountryName,mozillaHomeLocalityName,mozillaHomePostalCode,mozillaHomeState,mozillaHomeStreet,mozillaHomeStreet2,mozillaHomeUrl,mozillaNickname
by dnattr=seeAlso write
by group="cn=LDAPAdmin,dc=cgl,dc=ucsf,dc=edu" write
by * read
# Sample access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
# Directives needed to implement policy:
access to dn.base="" by * read
access to dn.base="cn=Subschema" by * read
access to *
by self write
by group="cn=LDAPAdmin,dc=cgl,dc=ucsf,dc=edu" write
by users read
by anonymous read
sasl-regexp
uid=(.*),cn=cgl.ucsf.edu,cn=gssapi,cn=auth
uid=$1,ou=Accounts,dc=cgl,dc=ucsf,dc=edu
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., "access to * by * read")
#
# rootdn can always read and write EVERYTHING!
#######################################################################
# ldbm database definitions
#######################################################################
database bdb
suffix "dc=cgl,dc=ucsf,dc=edu"
rootdn "cn=Manager,dc=cgl,dc=ucsf,dc=edu"
# Cleartext passwords, especially for the rootdn, should
# be avoid. See slappasswd(8) and slapd.conf(5) for details.
# Use of strong authentication encouraged.
rootpw ************************
# The database directory MUST exist prior to running slapd AND
# should only be accessible by the slapd and slap tools.
# Mode 700 recommended.
directory /usr/local/var/openldap-data
mode 700
# Indices to maintain
index uid pres,eq,approx,sub
index cn,sn,mail pres,eq,approx,sub
index eduPersonPrincipalName pres,eq,approx,sub
index mailRoutingAddress pres,eq,approx
index krbName pres,eq,approx
index givenName pres,eq,sub
index ucsfIDNumber pres,eq
index objectClass eq
index memberUID eq
index gidNumber eq
#
# Tuning
#
cachesize 5000
# Checkpoint every 10K or 60 minutes
checkpoint 10000 60
idlcachesize 5000
# Don't use memory mapped files
shm_key 119
#######################################################################
# Set up database replication
#######################################################################
replica uri=ldap://cgl.ucsf.edu:389
bindmethod=sasl saslmech=GSSAPI
replogfile /usr/local/var/openldap-data/replog
CGL LDAP Configuration File (/usr/local/etc/openldap/slapd.conf)
The LDAP schema employed by CGL is designed to provide for Web
Authorization requirements as well possible future uses for system
level authorization, user identity information, and possibly system
and printer information. Some of the more general directory services
and identity management functions are discussed in more detail
below. This section will focus on web
authorization, which was our primary requirement for LDAP.
An LDAP repository is essentially a hierarchically organized
data store whose contents are restricted by a set of object classes.
Each object class defines a set of required and optional
attributes, which themselves are defined to adhere to a specific
data format or content. The hierarchical organization is not
enforced by any specific data elements, rather, the Distinguished
Name (DN) of a record in the database is
hierarchically defined. For example, the DN for the web
group sacs is: cn=sacs,ou=Web Groups,ou=Groups,dc=cgl,dc=ucsf,dc=edu.
All elements contained within the CGL LDAP repository end with
dc=cgl,dc=ucsf,dc=edu, which is the BASE of the
server. The ou (Organizational Unit) elements after that
define the actual hierarchy. The data in the Web Groups organizational
unit is keyed by the cn (Common Name), which in this case is
sacs.
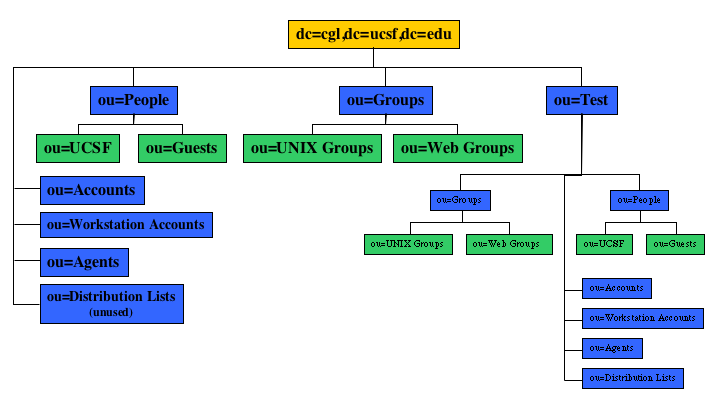
Figure 3 - CGL LDAP Schema
The organization of the CGL LDAP repository is shown in Figure 3. For
the purposes of web authorization, we are only concerned with
the Web Groups and the Accounts organizational units.
These are the two branches of the LDAP repository that are referenced
by the apache web server to determine if an authenticated user is
a member of an authorized web group. An example Accounts data
entry is shown below. The primary
source for this data is the /etc/passwd
file on socrates, but it has been enhanced with a number
of additional data items, including the ucsfIDNumber,
which provides a link into the People branch of the repository.
# scooter, Accounts, cgl.ucsf.edu
dn: uid=scooter,ou=Accounts,dc=cgl,dc=ucsf,dc=edu
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: inetLocalMailRecipient
objectClass: posixAccount
objectClass: cglAccount
objectClass: kerberosSecurityObject
# posixAccount attributes
uid: scooter
uidNumber: 170
gidNumber: 10
homeDirectory: /home/socr/a/scooter
gecos: Scooter Morris
loginShell: /usr/local/bin/bash
# person attributes
cn: Scooter Morris
cn: John "Scooter" Morris
givenName: Scooter
sn: Morris
# inetOrgPerson attributes
mail: scooter@cgl.ucsf.edu
# inetLocalMailRecipient attributes
mailRoutingAddress: scooter@cgl.ucsf.edu
mailHost: socrates.cgl.ucsf.edu
# kerberosSecurityObject attributes
krbName: scooter@CGL.UCSF.EDU
# cglAccount attributes
apple-authAuthority: ;Kerberosv5;;scooter@CGL.UCSF.EDU;CGL.UCSF.EDU;
isLocked: FALSE
irixHomeDirectory: /home/spin/scooter
ucsfIDNumber: 023387608
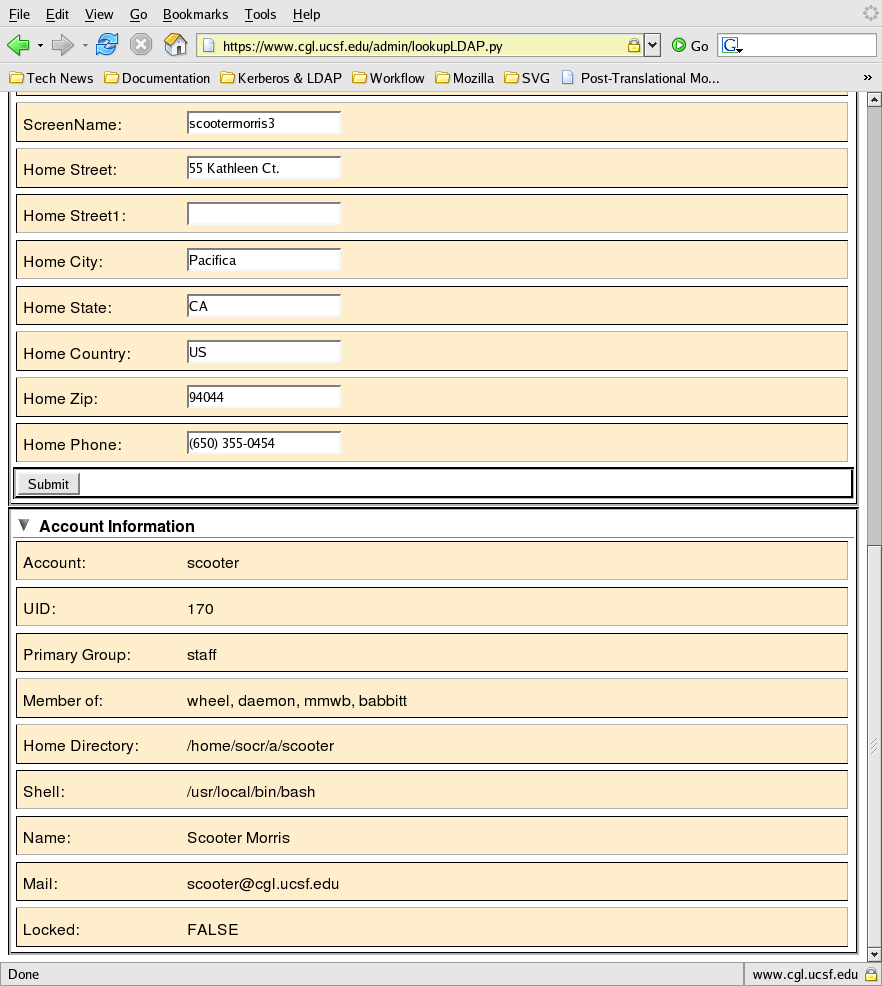
Example Accounts Data Entry
Each of the objectClass attributes enables certain data
attributes within the entry, which have been designated with
comments in the example. As much as possible the Accounts
objectClass attributes reflect standard and excepted
usage for Unix systems. Two additional object classes have
been added to support specific applications at CGL. The
first is the kerberosSecurityObject, which provides
the definition for the krbName attribute to provide
a link to the Kerberos principal that goes along with this
account. The second object class is the cglAccount
object class, which provides the definitions for some
attributes which we use specifically within the CGL
environment. The first of these is apple-authAuthority,
which is defined by Apple Computer and is used to provide
information to MacOS X computers that indicates how this
user should be authenticated. The second is isLocked
which is used to signal that this account has been disabled
for administrative purposes. The third is irixHomeDirectory
which is used to indicate where this user's home directory
should reside on our Irix workstations. The final addition
is the ucsfIDNumber which provides a link into the
People branch, as well as providing a key which can
be used to link into the UCSF LDAP repository.
# sacs, Web Groups, Groups, cgl.ucsf.edu
dn: cn=sacs,ou=Web Groups,ou=Groups,dc=cgl,dc=ucsf,dc=edu
objectClass: top
objectClass: posixGroup
gidNumber: 101
cn: sacs
owner: uid=johns,ou=Accounts,dc=cgl,dc=ucsf,dc=edu
owner: uid=scooter,ou=Accounts,dc=cgl,dc=ucsf,dc=edu
memberUid: tef
memberUid: conrad
memberUid: burling
memberUid: gerlt
memberUid: babbitt
memberUid: ortiz
memberUid: pett
memberUid: bic
memberUid: barondes
memberUid: brc
memberUid: ccwang
memberUid: craik
memberUid: zemin
memberUid: jengel
memberUid: faynboym
memberUid: inada
memberUid: goddard
memberUid: yoshi
memberUid: salter
memberUid: scanlan
memberUid: yizhang
memberUid: pcaldera
memberUid: valerie
...
description: SACS Web Group
Example Web Groups Data Entry
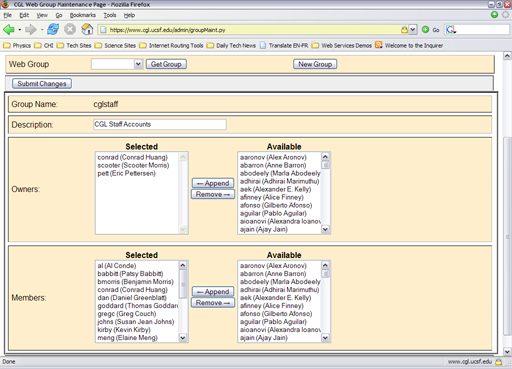
The Web Groups branch is simple in comparison to the
Accounts or People branches. The posixGroup
object class provides the definition for all of the attributes.
The key attributes are the owner attributes, and memberUid
attributes, and the description attribute. The entry is
keyed by the cn attribute, as discussed above. The owner
attributes and the description attribute are used by the LDAP group maintenance web page discussed
below. The memberUid attributes are used to determine group
membership. The LDAP server utilizes the SASL plug-in security
architecture to authenticate users. One of the mechanisms supported
by SASL is the KRB5-GSSAPI mechanism. This allows LDAP to utilize
Kerberos to authenticate, and enables single sign-on for LDAP
modifications and priviledges.
4. Periodic scripts
There are two periodic scripts that run that are related to LDAP. The first of these
is the LDAP update script. This script is run from periodic every night. As can
be seen from the script code below, the script gets credentials, then runs a python program
that reads the unix group file, the unix password file, and pulls information from the UCSF
LDAP repository. This information is used to create updated Account, People, and
unixGroup files, which are then imported into the LDAP repository. The results of all of
the imports are stored in /var/adm/ldapUpdate.log.
#! /bin/ksh -p
# This script updates the cgl LDAP repository from the
# passwd, group, and UCSF LDAP store
# Get our identity
/usr/local/bin/kinit -k -t /usr/local/etc/.rootkeys -p ldapbot
# scribble in tmp
cd /tmp
# First, run the ldap script, this will output the files
# account.ldif, people.ldif, unixGroup.ldif, and wAccount.ldif
# At this point, we only use the first three
/usr/local/etc/ldap_getPeople.py -t ldap
# Now update the data
rm -f /var/adm/ldapUpdate.log
/usr/local/bin/ldapmodify -c -f account.ldif > /var/adm/ldapUpdate.log
/usr/local/bin/ldapmodify -c -f people.ldif >> /var/adm/ldapUpdate.log
/usr/local/bin/ldapmodify -c -f unixGroup.ldif >> /var/adm/ldapUpdate.log
/usr/local/etc/periodic/daily/05.ldapUpdate.local
The second important script is run directly from periodic to control
the exact timing of its execution. This script stops both the slapd
daemon (LDAP server) and the slurpd daemon (replication server) so
that the log files can be reset, and the unused Berkeley DB database log
files can be purged. This is important as these files have a tendency to
build up over time, use a great deal of disk space.
#!/bin/sh
PATH=/usr/bin:/usr/sbin
export PATH
host=`caa_stat slapd | grep STATE=ONLINE | awk '{ print $NF }'`
caa_stop -f slapd
# Not sure why this sometimes needs to be run twice
rsh $host "/usr/local/BerkeleyDB.4.2/bin/db_recover -h /usr/local/var/openldap-data/"
rsh $host "/usr/local/BerkeleyDB.4.2/bin/db_recover -h /usr/local/var/openldap-data/"
rsh $host "/usr/local/BerkeleyDB.4.2/bin/db_archive -d -h /usr/local/var/openldap-data/"
caa_start slapd -c $host
caa_start slurpd -c $host
/usr/local/etc/periodic/scripts/ldap_clean